Kymera Systems Blog
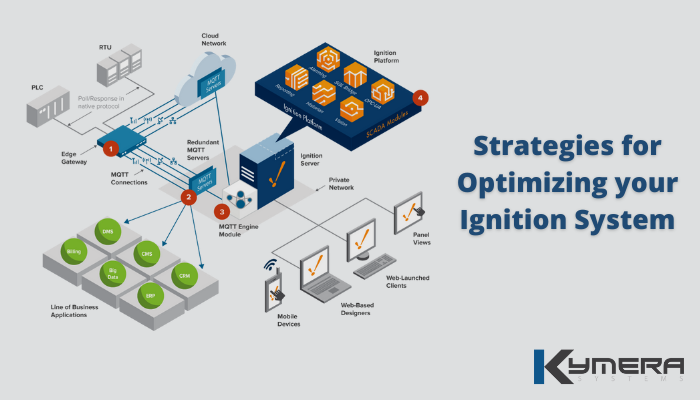
Strategies for Optimizing your Ignition System
What is Ignition? Ignition, by Inductive Automation, is a web-based deployment industrial application server software that acts as a central hub resulting in total system integration. This software platform can [...]
Alarming Growth, the Benefits of Alarm Rationalization
What is an Alarm? An alarm is defined as an event in which a person is notified with adequate time to prevent a shutdown activity. Alarming Growth Alarm growth is [...]
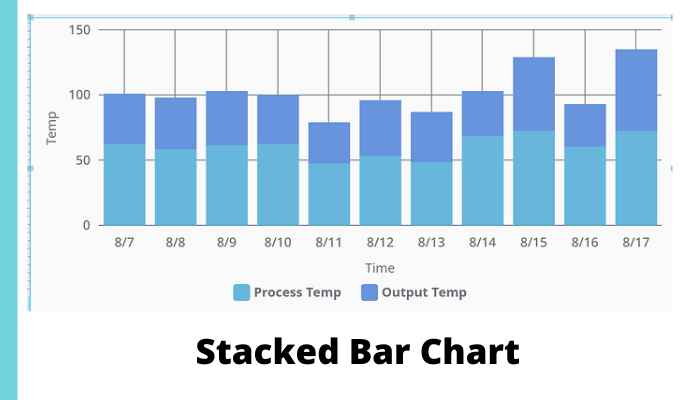
How to Create a Stacked Bar Chart in Perspective?
Our goal is to plot both process temp and outside temp represented as bars, one on top of the other, aka a stacked bar chart. A successful implementation will look [...]
6 Things You Must Know That Showcase the Importance of Cybersecurity
In our daily life, cybersecurity is very important. Cybersecurity is an umbrella term that covers all the technologies and processes used to keep computer systems, networks, devices, and electronic data [...]
Why Java is the Popular Programming Language in the World?
Java is the most universal programming language, which has certainly taken first situations in quite a while for a long time. Java is one of the most popular programming languages [...]
The Threat of IIoT Cyber Attacks
In the case of many industrial settings, the IIoT is considered the answer for numerous challenges. The connectivity that’s the result of it assists in efficiency, productivity, and profitability. When [...]
The Use Scenarios for IIoT Edge Are Defined, but Not the Standards
In any IIoT, edge computing occurs wherever it needs to, and the business itself determines when and where computing happens. That was the conclusion of the Industrial Internet Consortium’s (IIC) [...]
The Main Reasons Behind IIoT Vulnerability to Cyberattacks
The fact is that we see a significant increase in the number of attacks on both the industrial control systems (ICS) and the operational technology (OT) side of the Industrial [...]