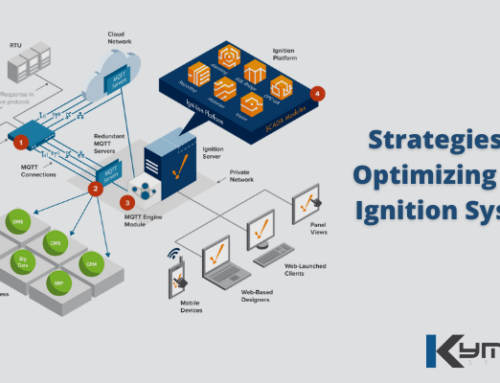
Control system cyber attacks in industrial facilities have become more destructive and dangerous. Besides the possibility of causing environmental damage, poor quality and loss production, and safety risks, the intrusions in Industrial Control Systems (ICS)/Supervisory Control and Data Acquisition (SCADA) could represent a severe threat to human life and safety in the most extreme case.
This June, the presentation by INSIGNIA researchers at the BSides conference emphasized that ICS could be exposed to remote hackers, physical manipulation, and local attacks. From the days of X21 connections and proprietary equipment, the presentation reviewed 25 years of the industrial control kit before talking about proof-of-concept attacks.
More Cyberattacks on Critical Infrastructure
In recent months, cyber intrusions on critical industrial infrastructure have increased with attackers creating threats to target those specific systems – WannaCry, Triton, and IndustroyerCrashOverride. The hacks in Ukraine showed us the damage that can be done through cyber hacks when the attackers were able to shut down and compromise systems. The attackers learn what do and don’t work and improvements needed for the next attack with each incursion.
That means that one cannot know when the next attack will happen because it could be around the corner. Not investing in cybersecurity measures carries potential consequences that could be severe and numerous. By being able to identify and mitigate potentially dangerous behavior, critical infrastructure operators need to keep track of the new destructive malware that is attackers develop.
Can Cybersecurity Technologies Help?
Wireless devices, including access points, gateways, and industrial routers as well as tablets and smartphones used by operators and engineers, are vulnerable to cyber attacks. It’s because the devices weren’t designed with that kind of security in mind.
Artificial Intelligence (AI) and machine learning are examples of innovation and implementation of new security technologies. These technologies are a massive stepping stone toward reliable and safe critical infrastructure. To detect any anomaly that detracts from expected patterns of behavior; companies should conduct active monitoring for anomalies and establish a baseline of ICS network communications. Securing industrial processes and networks have unique needs that these advanced technologies meet. They help reduce the cybersecurity skills gap and integrate with IT security infrastructure to bridge the OT/IT divide.
Why are the SCADA Systems Prone to Cyberattacks?
A typical SCADA system connects to the Internet with a unique IP. That means that these systems should have identity and access management systems, data-diodes, and firewalls. Many systems can’t withstand security scans and probes because they don’t include security coding approaches. Some systems allow for ‘brute force’ login attempts as they don’t have password timeouts, while necessary ICS block out may lead to system crashes. Attackers see the real-time security system as weak, and once they own the system, they can manipulate the controlled logic. The outcome can be irreparable even if all controllers are duplicated. The cyber attack changes the logic because multiple safety interlocks can be ignored.
With some protective mentoring technology supported by organization process and policies coupled with right analysts, it is possible to retain the full situational awareness of the nature of the attack. What determines the success of a plant? It is the degree of success of the control room operators who need to perform their tasks efficiently, securely, and safely.